Axios Codebook

September 06, 2022
Happy Tuesday! Welcome back to Codebook — and yes, I promise, today is actually Tuesday, not Monday.
Today's newsletter is 1,478 words, a 5.5-minute read.
1 big thing: Protecting water from cyberattacks
Illustration: Brendan Lynch/Axios
The Environmental Protection Agency's effort to secure the country's water supply from cyberattack faces giant hurdles.
They include: The water system's low government funding and staffing levels, a heavy reliance on legacy IT, and the patchwork nature of the tens of thousands of local U.S. water authorities.
Driving the news: The EPA submitted its initial plan for tackling water security to Congress last month, laying out which systems it would slot for technical assistance first during a cyberattack.
- The agency is expected to roll out new rules this fall requiring state officials to include cybersecurity concerns in their existing water inspections, an official told E&E News.
Between the lines: The EPA faces different challenges than other agencies writing cybersecurity rules for the utilities they regulate because the U.S.'s water systems are so widely distributed and isolated.
- The country has roughly 148,000 public water systems.
- Most of those water systems operate through state and local governments that have their own budget constraints and priorities.
Those states and cities need to have the resources and motivation to prioritize water cybersecurity to make any blanket EPA federal regulations effective, says Padraic O'Reilly, co-founder and chief product officer at critical infrastructure cyber firm CyberSaint Security.
- Bryan Ware, former assistant director of cyber at the Cybersecurity and Infrastructure Security Agency, tells Axios that water system operators in small to medium-size towns have small IT teams, making it difficult for them to prioritize cyber protections.
Threat level: While the distributed water system makes it nearly impossible for a malicious hacker to take down the entire U.S. supply in one fell swoop, hackers can still wreak havoc on small to medium-size towns' water supplies.
- In February 2021, a hacker was able to break into the computer system running the water system serving 15,000 people in Oldsmar, Florida, and tamper with the amount of sodium hydroxide in the supply.
- Last month, a U.K. water supplier serving 1.6 million people said its offices were disrupted after a cyberattack.
The intrigue: The EPA faces its own resource shortages, hindering its ability to establish and enforce tough cybersecurity rules for water systems.
- At least one estimate suggests the agency spends $7 million on cybersecurity operations within the Office of Water. Experts say that's nowhere near enough.
- The EPA has asked Congress for more in next year's budget, including $25 million for a new grant program to build out and improve water cybersecurity infrastructure.
Yes, but: The EPA can still get creative with its regulatory approach.
- In its August report to Congress, the agency said that it plans to work with CISA to help water systems mitigate and recover from a cyberattack.
- Politico reported last month that the agency is eyeing rules similar to the TSA guidelines for pipelines, which are more flexible and allow operators to submit their own plans for addressing common cybersecurity problems.
- Industry groups like the American Water Works Association have been pushing the EPA to lean more on CISA’s free resources for critical infrastructure providers, including providing cyber hygiene scans.
- A spokesperson for the National Security Council tells Axios the White House and EPA are working with Congress on solutions to help better train and staff water security professionals.
What's next: The EPA is still mulling what form broad federal rules for water operators should take, as federal officials work to help low-resourced water operators make cybersecurity a higher priority.
- As Congress returns from summer recess this week and begins budget talks, funding the EPA's cybersecurity efforts will be one item on the long agenda.
2. Cloudflare drops Kiwi Farms harassment site
Photo: David Paul Morris/Bloomberg via Getty Images
Web infrastructure and security services provider Cloudflare announced Saturday it was immediately blocking the Kiwi Farms site known for organizing the harassment and targeting of transgender people, Axios' Scott Rosenberg reports.
Driving the news: In the face of an activist campaign pressing the company to stop providing services to Kiwi Farms, Cloudflare had seemed to be digging in its heels, per an Aug. 31 blog post by CEO Matthew Prince.
Yes, but: "The rhetoric on the Kiwi Farms site and specific, targeted threats have escalated over the last 48 hours to the point that we believe there is an unprecedented emergency and immediate threat to human life unlike we have previously seen from Kiwi Farms or any other customer before," Prince wrote in a new post Saturday.
Why it matters: Cloudflare has long held that its role as a provider of back-end website services means that it should not play a role in assessing or censoring the content its customers distribute.
- But the company has also withdrawn services in the past from customers, including the Nazi Daily Stormer website after the 2017 Charlottesville rally. In 2019, Cloudflare dropped the 8chan troll haven after mass shooters used the site to distribute racist "manifestos."
Catch up quick: Kiwi Farms is a 10-year-old site that emerged from 8chan and has been used to organize campaigns aimed at trans, autistic and other individuals. In several cases, targets of such campaigns have committed suicide.
- Cloudflare's services are widely used by website publishers to distribute content efficiently and to protect their sites from denial-of-service attacks.
The latest: After spending most of the long weekend offline, Kiwi Farms returned early Tuesday at a new web address and with a new service provider, VanwaTech, based in Vancouver, Washington.
- The company, founded in 2019, per Bloomberg, has a record of hosting controversial and far-right sites.
3. TikTok data may have leaked, researchers say
Illustration: Aïda Amer/Axios
Researchers at BeeHive CyberSecurity tell Axios they're investigating claims of a possible breach involving TikTok user data.
The big picture: The scope, size and validity of the reported data breach are unclear, but screenshots of the leaked data files shared via Twitter on Sunday include PayPal information, marketing data and user statistics.
What they're saying: A TikTok spokesperson told Axios on Monday that the company's security team didn't find any evidence of a breach at the company after investigating the claims.
- “We have confirmed that the data samples in question are all publicly accessible and are not due to any compromise of TikTok systems, networks or databases," the spokesperson said in a statement. "The samples also appear to contain data from one or more third-party sources not affiliated with TikTok."
Details: BeeHive CyberSecurity, a group that scans and researches security flaws in products, told Axios in an email Monday that it had received a report over the weekend from hacker group AgainstTheWest claiming it had gained access to a temporary storage location containing TikTok and WeChat data.
- To confirm access, the group sent BeeHive a sample of the logs it had access to, but it doesn't appear the group shared details about how it found this data.
- BeeHive described the group as "reputable" and claimed the data sample it shared would be difficult to fabricate.
- AgainstTheWest is "still exporting data, so we'll be able to confirm the scope of this breach as soon as the influx of new data ceases," BeeHive said.
Why it matters: As researchers investigate the claims — which have since gone viral on social media — the discussion of possible user data exposure could add to Washington's concerns about the privacy and security practices at the Chinese-owned social media company.
- Last week, Microsoft researchers shared details about a since-patched vulnerability in TikTok's Android app.
- The Biden administration is expected to issue an executive order as early as this month that could limit how much data Chinese companies, including TikTok, can collect about U.S. citizens, Semafor reported.
The intrigue: AgainstTheWest's discovery of the storage location is still fresh, meaning the scale, scope and validity of the information it contains remain unclear.
4. Catch up quick
@ D.C.
💰 The Irish Data Protection Commission is fining Instagram €405 million ($401 million) for violating Europe's privacy law. (Politico)
🏛 California is attempting to become a "data sanctuary" after passing two bills restricting other states' law enforcement from collecting data about people who get abortions or gender-affirming care in the state. (Protocol)
@ Industry
💔 Peter Eckersley, the encryption and privacy pioneer behind projects like HTTPS Everywhere and Privacy Badger, died at 43 over the weekend. (Risky Business)
👨🏻⚖️ Joe Sullivan, the former Uber security chief facing felony charges for allegedly mishandling a data breach, will stand trial starting this week. (New York Times)
💼 Despite pushback from brokers and academics, Lloyd's of London is defending its new policy to exclude state-backed cyberattacks from insurance policies. (Financial Times)
@ Hackers and hacks
🍎 Los Angeles Unified School District, the second-largest district in the country, said over the weekend it was the target of a ransomware attack. (BleepingComputer)
⚡️ Italy's energy agency said its website is back online after suffering a ransomware attack last week. (Bloomberg)
📲 Samsung said it suffered a data breach in late July that exposed customers' contact information and product registration numbers. (Axios)
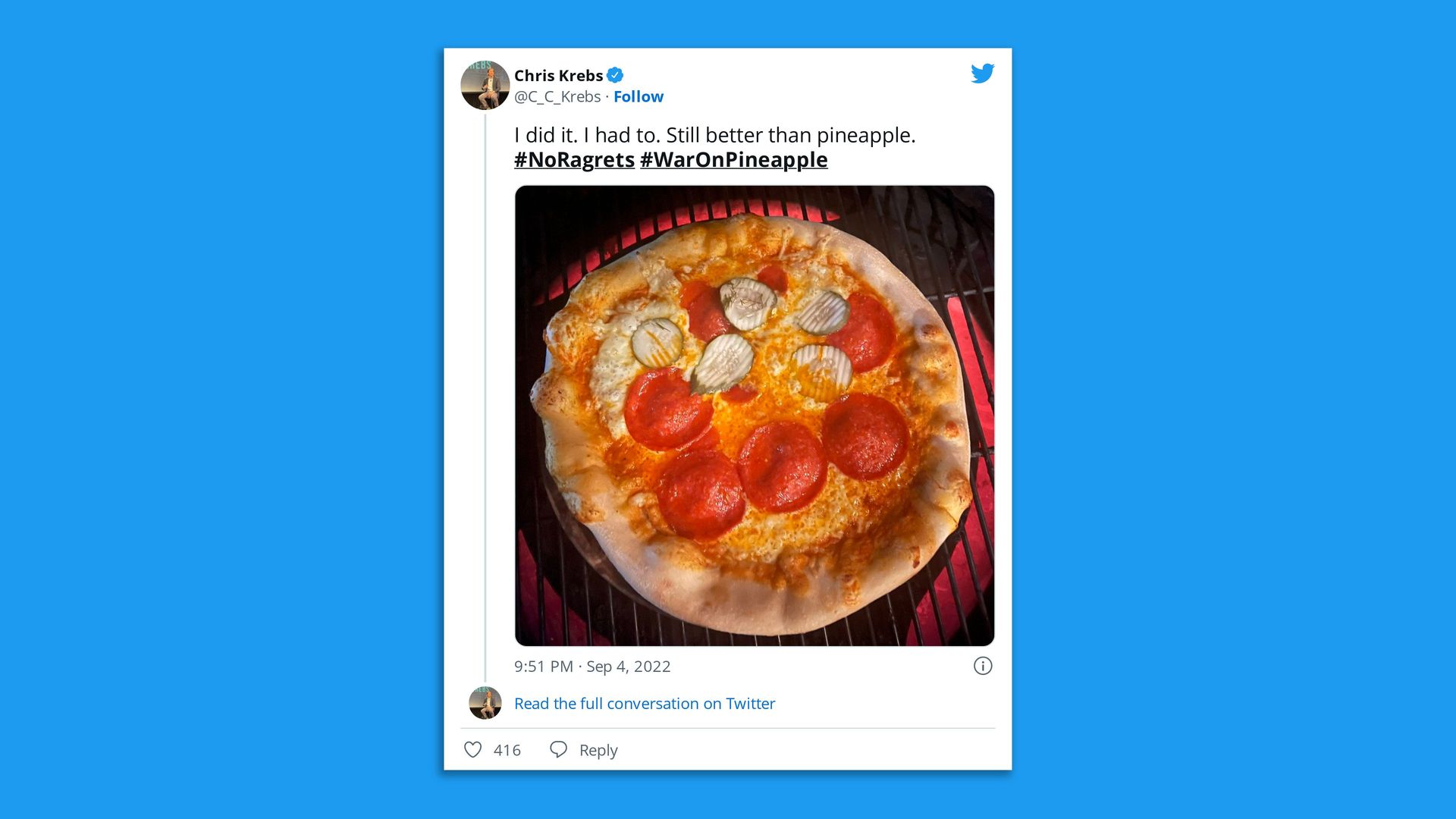
5. 1 fun thing
Screenshot: @C_C_Krebs/Twitter
For those keeping track at home, the ongoing cybersecurity community debate over acceptable pizza toppings has turned to a new entrant: Pickles???
☀️ See y'all on Friday!
If you like Axios Codebook, spread the word.
Sign up for Axios Codebook

Decode key cybersecurity news and insights. With Sam Sabin.