Axios Codebook

September 26, 2019
Welcome to Codebook, the most fascinating cybersecurity newsletter in the most fascinating timeline.
Today's Smart Brevity: 1,723 words, 6.5-minute read
1 big thing: $250M for election security is a fraction of what's needed
Illustration: Aïda Amer/Axios
Last week, Senate Majority Leader Mitch McConnell offered his support for a $250 million election security fund. By experts' estimates, that's only around 10% of what states will need between now and 2024 in order to protect elections from security threats.
The big picture: The County Commissioners Association of Pennsylvania says it will cost $125 million to replace unsecure voting machines in its state alone, meaning half the new funds could be spent on one small aspect of election security in just one state.
Driving the news: McConnell added his name last week to a bipartisan $250 million amendment to a pending appropriations bill, an abrupt change from his earlier thwarting of election cybersecurity bills.
The bare minimum cost of securing the U.S. election system is $2.153 billion over the next 5 years, according to an estimate by the Brennan Center at NYU Law School. Lawrence Norden, director of the Electoral Reform Program at Brennan, told Axios it will likely cost a similar amount every 5 years after that.
By the numbers: By the Brennan estimates, it will cost:
- $734 million to purchase voting machines that use paper ballots for the last few states, including Pennsylvania, that haven't already switched. Paper leaves an unhackable record of voter intent.
- $486 million for secure voter registration systems.
- $833 million for state and local election cybersecurity, including $55 million in county-level cybersecurity staffing, assuming 1 employee for every 10 counties, and $9.6 million for website security.
- $100 million for post-election audits.
This isn't just a voting machine issue: The public debate about election security often gets falsely reduced to swapping out machines without paper ballots for machines with them.
- "People find it easy to wrap their heads around paper ballots," said Norden. "But there are a lot of other ways that elections can be attacked that have nothing to do with voting machines. If you look at successful attacks across the world, they target voter databases and reporting systems."
Many of those costs repeat: "The equipment ages out. Voting machines have to be replaced every 10 years," Norden said.
- Staffing costs, web security and other expenses recur year-round, year after year.
- "People think that on Election Day, they just go and cast a ballot," said Earl Matthews, chief strategy officer at the security firm Verodin and a retired Air Force major general. "But that process actually began many months earlier."
The federal government doesn't have to bear the full cost of cybersecurity. In fact, most states would prefer some degree of autonomy in how they run elections.
- But states can't realistically fight off nations without a little more help.
- "The federal government has a responsibility to share," said Christopher Deluzio, director of policy at University of Pittsburgh's cyber center, who has written frequently about the cost of securing elections.
The politics: A GOP aide stressed to Axios that with the $250 million, the total amount of election security funding allotted to the states since 2018 exceeded $600 million.
- An earlier $380 million, already accounted for in the Brennan estimate, wasn't entirely new — it was money that was designated for election systems grants from legislation passed after the hanging chad debacle in Florida in the 2000 election.
- The House has sent more substantive plans to McConnell's Senate. The For the People Act, the first bill passed by the House this session, allotted nearly $1.6 billion for election security — including $1.5 billion for equipment and $55 million for "bug bounty" programs.
The bottom line: $250 million is a down payment on security, not the full bill.
2. Trump espouses half-remembered cyber conspiracy in Ukraine memo
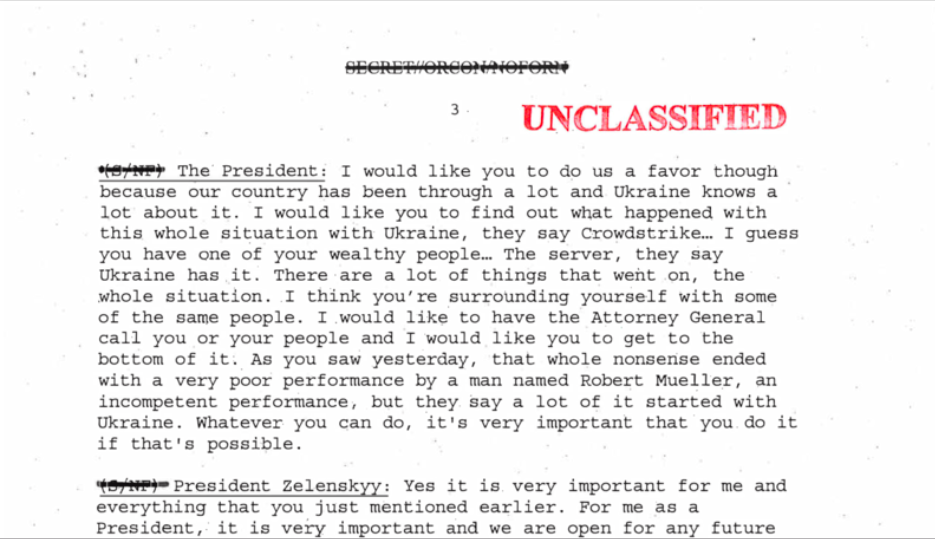
There are other concerning issues at play in the Ukraine memo released by the White House Wednesday. But don't overlook the part where President Trump appears to subscribe to an easily debunked conspiracy theory that he doesn't quite remember.
What they're saying: "I would like you to find out what happened with this whole situation with Ukraine, they say Crowdstrike... I guess you have one of your wealthy people... The server, they say Ukraine has it," reads Trump's comments to the Ukrainian president (ellipses from the original document).
CrowdStrike is the American company hired by the Democratic National Committee to investigate and expunge the hackers responsible for the 2016 breach. The firm is at the center of a number of right-wing conspiracy theories because it was the first to publicly release evidence that Russia perpetrated the digital trespass.
President Trump has expressed distrust in the firm by name since at least 2017, when he told AP he "heard it’s owned by a very rich Ukrainian."
- CrowdStrike is not owned by a very rich Ukrainian. It's a U.S. firm, now publicly traded, built on U.S. venture capital.
- There is, however, a right-wing conspiracy attempting to show that founder Dmitri Alperovitch, who was a nonresident fellow at the Atlantic Council think tank in 2016, was somehow compromised by Ukrainian businessman and Atlantic Council donor Victor Pinchuk.
- It's a half-baked theory. In 2015, for example, Pinchuk donated $150,000 to the Trump Foundation.
Whatever "they say," Ukraine does not have the DNC server that Trump frequently claims — incorrectly — the FBI forgot to investigate.
- There is no single server to hide in Ukraine. With modern computing, what people experience as a single server is actually dozens of different systems. Court documents show that the DNC decommissioned well over 100.
- The FBI received a digital image of the servers — a complete record of what was on the unwieldy farm of physical computers. Physically obtaining the servers would provide no new information.
It is standard practice for an incident response group like CrowdStrike to handle the initial investigation into who hacked a system while booting hackers from the system.
- That investigation is well-documented and, even under a new FBI director, is often welcomed by a bureau that would rather spend its resources investigating things only the bureau can investigate than do busy work incident responders can do.
Why it matters: For a president to keep repeating that something so easily explained was amiss in the Russia investigation is profoundly concerning.
- Take away any evidence CrowdStrike came within a mile of, and there is still more than enough evidence against Russia.
- Other security firms — competitors, also not owned by Ukraine — independently tied the attacks to Russia.
- Intelligence agencies have visibility on Russian operations from the inside.
- It's time to give this up.
3. Tortoiseshell group hacks U.S. vets
Tortoiseshell, an espionage group first discovered by Symantec earlier this month, used a fake veterans' job site to implant malware on former service members and other job seekers, Cisco's Talos Labs reports.
The big picture: Symantec first noticed the group in attacks on Saudi IT providers.
4. In case you missed it
Look out, it's LookBack (Proofpoint): Employees at 17 U.S. utilities were targeted by a phishing campaign containing the LookBack malware, according to Proofpoint.
- This is the second known campaign from the group behind LookBack, which sends official-looking emails from the organizations providing required employee certifications that spew malware.
- Proofpoint does not know the identity of the attacker, but believes the group is involved with espionage. "It has the hallmarks of an APT [advanced persistent threat, a government-run group]," Sherrod DeGrippo, senior director of the threat research and detection team at Proofpoint, told Codebook.
Bumbling social media scheme hit Hong Kong protesters (Axios): Researchers at Graphika uncovered an amateurish social media campaign targeting the Hong Kong protests that spanned across hundreds of accounts on several mainstream Western platforms.
- "The campaign focused on video content with short videos supporting police and attacking protesters," Graphika's Ben Nimmo told Axios, adding that other elements of the campaign dated back to at least 2018 and targeted billionaire emigrant Guo Wengui.
- Graphika believes the Chinese government did not run the campaign it has dubbed "Spamouflage Dragon" due to its general clumsiness. The accounts seemed to interact mostly with each other and struggled to generate external attention.
- Nimmo said the campaign was most likely run by amateurs or a private social media campaign firm.
- YouTube, Facebook and Twitter removed assets belonging to the "Spamouflage Dragon" in August.
Facebook election team tours Washington: Facebook's election security team will finish 3 days of meetings with policy staff, political parties, national security officials and candidates Thursday, according to a person familiar with the meetings.
- Lawmakers were particularly interested in issues like ad transparency, deep fakes and issues with academic access to data that Facebook has promised, as well as issues about partnerships between Facebook and private groups like disinformation researchers.
- Facebook is hoping to keep communications lines open with D.C. as politicians enter election season.
- This week's events follow Facebook founder Mark Zuckerberg's meetings with lawmakers last week in D.C. and meetings with federal law enforcement and intelligence agencies at Facebook's California headquarters 2 weeks ago.
Russian hacker pleads to data theft (DOJ): Andrei Tyurin pleaded guilty in New York to stealing data of more than 100 million victims from financial institutions.
Fancy Bear's ace hackers are back and fancier than ever (ESET): Fancy Bear, one of the Russian hacker groups believed to have hacked the Democratic National Committee in 2016, debuted new tools in a recent round of breaches.
- The group debuted updated features in the Zebrocy malware in attacks against embassies and ministries of foreign affairs in Eastern Europe and Central Asia.
Soccer leaker charged as hacker (New York Times): Rui Pinto, whose leaked documents on European soccer stars led to the reopening of a sexual assault charge against a prominent player in the U.S., was charged with nearly 150 counts of hacking in Portugal.
North Korea is hacking ATMs (Kaspersky): The famed Lazarus Group, often involved in Pyongyang's attempts to steal capital that sanctions now make it impossible to otherwise obtain, is using new malware to rob ATMs, notes Kaspersky.
5. Odds and ends
- Required reading: NPR goes deep inside the U.S. operation to hack ISIS. (NPR)
- 27 nations agree to cybersecurity norms in a statement with not-too-subtle references to China and Russia. (CNN)
- Your Match.com suitor may have been a robot, alleges the FTC. (FTC)
- Malware full of anime references is plaguing the Kuwaiti shipping and transportation industry. (Palo Alto Networks Unit 42)
- Headline of the day: "Interview with the guy who tried to frame me for heroin possession." (Krebs on Security)
- Google made a huge leap forward in quantum computing, but encryption is safe (for now). (Wired)
- China has a new Windows backdoor. (Cylance)
Codebook reader pick the Cleveland Browns lost to the LA. Rams after a 4th and 9 draw play even the Browns' coach admitted was the wrong call. Someone — I hope it wasn't any of you — lost $500,000 on the bout.
We'll be back next week.
Sign up for Axios Codebook

Decode key cybersecurity news and insights. With Sam Sabin.
