Axios Codebook

April 12, 2018
Welcome to Axios Codebook. Please reply to this email with any tips, comments, secrets or Game Genie codes.
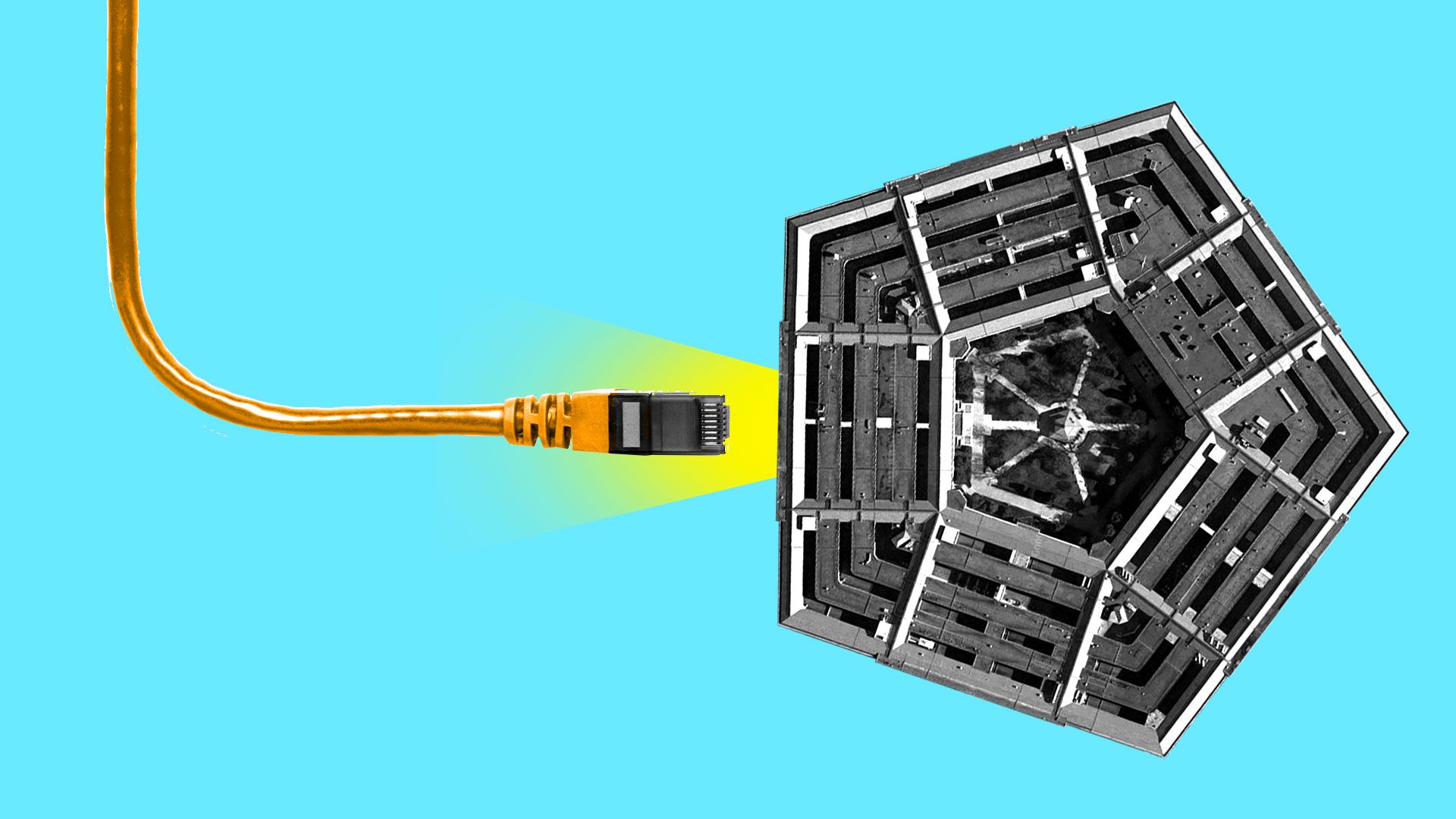
1 big thing: One cloud doesn't rule them all
Illustration: Lazaro Gamio/Axios
The Department of Defense took a lot of flak over recently announced plans to award a single contract for its massive cloud services project. Critics fear it will create a cloud monopoly.
Joe Bourgeois, who is Deloitte's managing director of federal technology strategy and architecture, says there might be an even bigger problem with awarding this humongous cloud contract to a single provider: Clouds aren't interchangeable, and fewer is less efficient.
"There's a feeling that the cloud is a commodity, and that one cloud equals efficiency. I'd like to fight that."— Doug Bourgeois, Deloitte
The big picture: The cloud, simply, is a way of renting computer resources rather than owning them — and letting someone else deal with maintaining the plumbing. The cloud makes it easier to scale your system up and down. (The IRS, notes Bourgeois, needs disproportionate computing power around tax day. Why pay for machinery that would sit idle in June?)
Operating in the cloud is typically cheaper, and more secure, than running department-owned equipment. With IT modernization funds now in place and laws mandating departments to move, government agencies are ready to make a switch.
The catch: The problem, Bourgeois said, is that agencies have a tendency to view computing resources as interchangeable, like pencils. But different computing operations rely on different physical hardware: the fastest computing hardware for word processing is different from the fastest hardware for mining bitcoin — and neither is best equipped to run machine-learning applications.
"Due to the diversity of federal workloads, they will eventually want multiple clouds," Bourgeois said.
The intrigue: The Department of Defense is trying to move to a single cloud provider, and the bidding process, many Amazon competitors quietly believe, was specifically structured for Amazon to win. (Read more on the Amazon controversy from Axios's Shannon Vavra.)
- If Amazon does win, then, based on the size of the DOD contract, some of the companies purchasing cloud services from IBM, Google, Microsoft and others fear their providers will lose so much government business that they'll need to shut down.
- Bourgeois wouldn't comment directly on the DOD contract. But he fervently believes a monoculture of cloud providers stifles innovation.
- "As long as different cloud providers try to differentiate their services, there should be a purpose for all of them," he said.
2. Maybe we'll get a cyber strategy by August
A Department of Defense official told lawmakers a long-awaited national cyber strategy might be released by late summer.
What they're saying: "It should be forthcoming in the near future. We are looking to then enhance our cyber posture approach, which we will be providing by August to sync with that national strategy," said Kenneth Rapuano, assistant secretary of defense for homeland defense and global security, during a House Armed Services Committee hearing Wedesnesday.
The big picture: The cybersecurity strategy has been in the works since the earliest days of the Trump administration. A 2017 executive order called for a number of reports to assess cybersecurity shortcomings and priorities.
- Late last year, then-White House homeland security adviser Tom Bossert said that the policy would take as long as it was going to take, but when it finally arrived it would follow the priorities of the executive order.
- Those priorities include securing federal networks and critical infrastructure, and developing a set of international cyber norms —red lines for nations conducting cyber operations, including espionage and destructive campaigns.
Tom Bossert resigned his post this week. He was replaced in an acting role by White House cyber czar (and delightfully unironic Christmas light enthusiast) Rob Joyce. These were only two of a number of national security posts shuffled recently, led by the arrival of new national security adviser John Bolton.
- It's unclear whether the staffing changes will affect a strategy drawn up under Bossert's leadership.
3. Emergency sirens hackable, loud
Bad news for people who like to sleep: Researchers claim the emergency sirens that dot San Francisco were, until recently, vulnerable to hackers.
The details: Before the ATI Systems' sirens go "BRWAAAAAH," the city sends an alert via a radio signal. That signal had not been encrypted until ATI provided a patch the city installed a few days ago.
The danger: Bastille, the firm that uncovered the issue and dubbed it "SirenJack," presented the attack as if anyone would be able to pull it off. The sirens are regularly tested at noontime, but unexpected alarms would be, at best, extremely annoying and, at worst, terrifying.
The fix: San Francisco says the vulnerability have been locally patched.
The intrigue: A representative from ATI disputed how easy the attack would have been to pull off in the wild, claiming that while the signal was unencrypted it was protected by frequency hopping. According to the representative, an attack might take years of prep time or physical access to a control center.
That doesn't entirely jibe with the story the city and Bastille tell. But even if an attack was unlikely, it would certainly have been unwelcome if someone managed to pull it off.
BRWAAAAAH! It would be really scary, right?
4. Pallone decries "privacy by press release"
Mark Zuckerberg appeas before the House Energy and Commerce Committee. Photo: Chip Somodevilla/Getty Images.
From the "it's possible something other than Diamond and Silk came up at the Facebook hearing" file: Frank Pallone, ranking Democratic member of the House Energy and Commerce Committee, punched his way through his opening statement at Wednesday's event, calling for new privacy regulation and questioning the committee's resolve to do anything about whatever issues arose during Mark Zuckerberg's testimony.
Take a gander at this conclusion: "My great fear is that we have this hearing today, there's a lot of press attention — and, Mr. Zuckerberg, you know, appreciate your being here once again — but, if all we do is have a hearing and then nothing happens, then that's not accomplishing anything.... I've just seen it over and over again — that we have the hearings, and nothing happens. So excuse me for being so pessimistic, mister chairman, but that's where I am," said Pallone.
In the meat of his opening statement, Pallone slammed Republicans for weakening privacy rules and called on his committee to pass new legislation.
- "Republicans here in Congress continue to block or even repeal the few privacy protections we have...their justification that those protections were not needed because the Federal Trade Commission has everything under control — well, this latest disaster shows just how wrong the Republicans are."
- Weakening these rules, he continued, allows companies to avoid making security upgrades until an inevitable press release apologizing for a crippling breach makes them impossible to avoid.
- "By not doing its job, this Republican-controlled Congress has become complicit in this nonstop cycle of privacy by press release."
How they're replying: "I think I thank the gentleman for his opening comments," replied Greg Walden (R-Ore.), the committee chair.
- Right after the hearing, Walden said: "I don’t want to rush into legislation minutes after having the first hearing of this magnitude, but certainly if they can’t clean up their act we’ll clean it up for them.”
5. "Operation Parliament" strikes Palestine, other regional players
Kaspersky Lab is tracking an espionage campaign targeting a number of countries in or relevant to the Middle East, with a particular focus on Palestine.
Kaspersky does not often speculate about attribution, and has not in this case. It does say that the attackers have tried to disguise their effort as the work of a less sophisticated regional player, the Gaza Cybergang.
The details: The campaign Kaspersky has dubbed "Operation Parliament" uses previously unseen malware spread through email phishing lures. The group has targeted largely government systems, with victims in the Palestinian Territories, Egypt, Jordan, the UAE, Saudi Arabia, Djibouti, Qatar, Lebanon, Chile, Somalia, Iraq, Morocco, Syria, India, Iran, Canada, the USA, the UK, Germany, Israel, Afghanistan, Serbia, Russia, Oman, Kuwait, South Korea and Denmark.
6. "Thousands" of sites compromised by FakeUpdates
"Thousands" of authentic sites running the WordPress, Joomla, and SquareSpace content management systems have been hacked to spew out malware, according to a blog post by Malwarebytes Labs.
Fake updates: Users who visit the compromised sites will be offered malicious updates for their web browsers. Those fake updates install Chtonic, malware used to steal banking logins. Malwarebytes has creatively dubbed the campaign of fake updates FakeUpdates.
7. Odds and ends
- Quantum physicists create actual, for real random numbers. Those stupid, not-really-random numbers you've been forced to soldier along with your whole life are for jerks. (The Register)
- TrendMicro is tracking some Mirai-like behavior out of China that attacks devices through default usernames and passwords. (TrendMicro)
- The DHS's biannual Cyber Storm exercise is go. (Axios)
- Cambridge Analytica has a new CEO. (Wall Street Journal)
- On the move: Former CIA director John Brennan joined an advisory board for SecureAuth and Core Security.
We'll be back next week, live from the RSA conference.
Sign up for Axios Codebook

Decode key cybersecurity news and insights. With Sam Sabin.